Achieving cloud resource optimization with trust-based access control: A novel ML strategy for enhanced performance
- PMID: 40678452
- PMCID: PMC12269507
- DOI: 10.1016/j.mex.2025.103461
Achieving cloud resource optimization with trust-based access control: A novel ML strategy for enhanced performance
Abstract
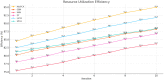
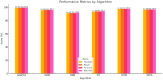
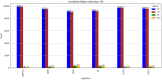
Cloud computing continues to rise, increasing the demand for more intelligent, rapid, and secure resource management. This paper presents AdaPCA-a novel method that integrates the adaptive capabilities of AdaBoost with the dimensionality-reduction efficacy of PCA. What is the objective? Enhance trust-based access control and resource allocation decisions while maintaining a minimal computational burden. High-dimensional trust data frequently hampers systems; however, AdaPCA mitigates this issue by identifying essential aspects and enhancing learning efficacy concurrently. To evaluate its performance, we conducted a series of simulations comparing it with established methods such as Decision Trees, Random Forests, and Gradient Boosting. We assessed execution time, resource use, latency, and trust accuracy. Results show that AdaPCA achieved a trust score prediction accuracy of 99.8 %, a resource utilization efficiency of 95 %, and reduced allocation time to 140 ms, outperforming the benchmark models across all evaluated parameters. AdaPCA had superior performance overall-expedited decision-making, optimized resource utilization, reduced latency, and the highest accuracy in trust evaluation among the evaluated models. AdaPCA is not merely another model; it represents a significant advancement towards more intelligent and safe cloud systems designed for the future.•Introduces AdaPCA, a novel hybrid approach that integrates AdaBoost with PCA to optimize cloud resource allocation and improve trust-based access control.•Outperforms conventional techniques such as Decision Tree, Random Forest, and Gradient Boosting by attaining superior trust accuracy, expedited execution, enhanced resource utilization, and reduced latency.•Presents an intelligent, scalable, and adaptable architecture for secure and efficient management of cloud resources, substantiated by extensive simulation experiments.
Keywords: AdaBoost; AdaBoost with Principal Component Analysis; Cloud computing; Dimensionality reduction; Machine learning; Principal Component Analysis; Resource optimization; Trust assessment; Trust-based access control.
© 2025 The Authors. Published by Elsevier B.V.
Conflict of interest statement
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Figures
References
-
- Alhomdy S., Thabit F., Abdulrazzak F.H., Haldorai A., Jagtap S. The role of cloud computing technology: a savior to fight the lockdown in COVID 19 crisis, the benefits, characteristics and applications. Int. J. Intell. Networks. 2021;2:166–174. doi: 10.1016/J.IJIN.2021.08.001. - DOI
-
- Nair M.M., Tyagi A.K. AI, IoT, blockchain, and cloud computing: the necessity of the future. Distrib. Comput. Blockchain Archit. Technol. Appl. 2023:189–206. doi: 10.1016/B978-0-323-96146-2.00001-2. - DOI
-
- Wang M., Zhang Q. Optimized data storage algorithm of IoT based on cloud computing in distributed system. Comput. Commun. 2020;157:124–131. doi: 10.1016/J.COMCOM.2020.04.023. - DOI
-
- Shukla D.K.R., Dwivedi V.K.R., Trivedi M.C. Encryption algorithm in cloud computing. Mater. Today Proc. 2021;37:1869–1875. doi: 10.1016/J.MATPR.2020.07.452. - DOI
-
- Alshammari S.T., Albeshri A., Alsubhi K. Building a trust model system to avoid cloud services reputation attacks. Egypt. Informatics J. 2021;22:493–503. doi: 10.1016/J.EIJ.2021.04.001. - DOI
LinkOut - more resources
Full Text Sources