A service-oriented microservice framework for differential privacy-based protection in industrial IoT smart applications
- PMID: 40783426
- PMCID: PMC12335493
- DOI: 10.1038/s41598-025-15077-7
A service-oriented microservice framework for differential privacy-based protection in industrial IoT smart applications
Abstract
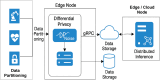
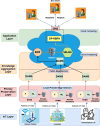
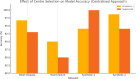
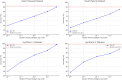
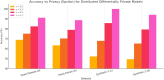
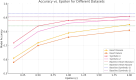
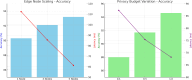
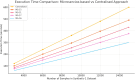
The rapid advancement of key technologies such as Artificial Intelligence (AI), the Internet of Things (IoT), and edge-cloud computing has significantly accelerated the transformation toward smart industries across various domains, including finance, manufacturing, and healthcare. Edge and cloud computing offer low-cost, scalable, and on-demand computational resources, enabling service providers to deliver intelligent data analytics and real-time insights to end-users. However, despite their potential, the practical adoption of these technologies faces critical challenges, particularly concerning data privacy and security. AI models, especially in distributed environments, may inadvertently retain and leak sensitive training data, exposing users to privacy risks in the event of malicious attacks. To address these challenges, this study proposes a privacy-preserving, service-oriented microservice architecture tailored for intelligent Industrial IoT (IIoT) applications. The architecture integrates Differential Privacy (DP) mechanisms into the machine learning pipeline to safeguard sensitive information. It supports both centralised and distributed deployments, promoting flexible, scalable, and secure analytics. We developed and evaluated differentially private models, including Radial Basis Function Networks (RBFNs), across a range of privacy budgets (ɛ), using both real-world and synthetic IoT datasets. Experimental evaluations using RBFNs demonstrate that the framework maintains high predictive accuracy (up to 96.72%) with acceptable privacy guarantees for budgets [Formula: see text]. Furthermore, the microservice-based deployment achieves an average latency reduction of 28.4% compared to monolithic baselines. These results confirm the effectiveness and practicality of the proposed architecture in delivering privacy-preserving, efficient, and scalable intelligence for IIoT environments. Additionally, the microservice-based design enhanced computational efficiency and reduced latency through dynamic service orchestration. This research demonstrates the feasibility of deploying robust, privacy-conscious AI services in IIoT environments, paving the way for secure, intelligent, and scalable industrial systems.
Keywords: Differential privacy; Distributed machine learning; Edge-cloud computing; Health care sector; Industrial Internet of Things (IIoT); Microservices architecture; Privacy; Radial basis function network (RBFN).
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests.
Figures






References
-
- Gad, A. G., Houssein, E. H., Zhou, M., Suganthan, P. N., & Wazery, Y. M. Damping-assisted evolutionary swarm intelligence for industrial IoT task scheduling in cloud computing. IEEE Internet Things J.. 11(1), 1698–1710 10.1109/JIOT.2023.3291367 (2024).
-
- Kaur, A. Intrusion detection approach for industrial internet of things traffic using deep recurrent reinforcement learning assisted federated learning. IEEE Trans. Artif. Intell.6(1), 37–50. 10.1109/TAI.2024.3443787 (2025).
-
- Samanta, A. & Nguyen, T. G. Trust-based distributed resource allocation in edge-enabled IIoT networks. IEEE Access13, 79694–79704. 10.1109/ACCESS.2025.3567068 (2025).
-
- Sun, Zongkun, Wang, Yinglong, Shu, Minglei, Liu, Ruixia & Zhao, Huiqi. Differential privacy for data and model publishing of medical data. IEEE Access7, 152103–152114 (2019).
-
- Acar, A., Celik, Z. B., Aksu, H., Uluagac, A. S. & McDaniel, P. Achieving secure and differentially private computations in multiparty settings. In 2017 IEEE Symposium on Privacy-Aware Computing (PAC), 49–59 (IEEE, 2017).
LinkOut - more resources
Full Text Sources

