PACKETCLIP: multi-modal embedding of network traffic and language for cybersecurity reasoning
- PMID: 40791311
- PMCID: PMC12336109
- DOI: 10.3389/frai.2025.1593944
PACKETCLIP: multi-modal embedding of network traffic and language for cybersecurity reasoning
Abstract
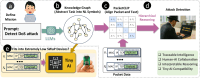
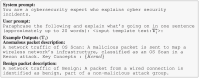
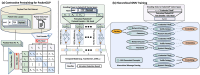
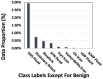
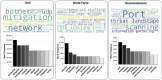
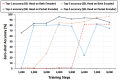
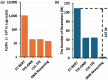
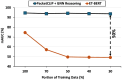
Traffic classification is vital for cybersecurity, yet encrypted traffic poses significant challenges. We introduce PACKETCLIP which is a multi-modal framework combining packet data with natural language semantics through contrastive pre-training and hierarchical Graph Neural Network (GNN) reasoning. PACKETCLIP integrates semantic reasoning with efficient classification, enabling robust detection of anomalies in encrypted network flows. By aligning textual descriptions with packet behaviors, PACKETCLIP offers enhanced interpretability, scalability, and practical applicability across diverse security scenarios. With a 95% mean AUC, an 11.6% improvement over baselines, and a 92% reduction in intrusion detection training parameters, it is ideally suited for real-time anomaly detection. By bridging advanced machine-learning techniques and practical cybersecurity needs, PACKETCLIP provides a foundation for scalable, efficient, and interpretable solutions to tackle encrypted traffic classification and network intrusion detection challenges in resource-constrained environments.
Keywords: contrastive pre-training; graph neural network; machine learning; multimodal; reasoning.
Copyright © 2025 Masukawa, Yun, Jeong, Huang, Ni, Bryant, Bastian and Imani.
Conflict of interest statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Figures

Similar articles
-
Encrypted traffic classification encoder based on lightweight graph representation.Sci Rep. 2025 Aug 5;15(1):28564. doi: 10.1038/s41598-025-05225-4. Sci Rep. 2025. PMID: 40764490 Free PMC article.
-
(H-DIR)2: A Scalable Entropy-Based Framework for Anomaly Detection and Cybersecurity in Cloud IoT Data Centers.Sensors (Basel). 2025 Aug 6;25(15):4841. doi: 10.3390/s25154841. Sensors (Basel). 2025. PMID: 40808005 Free PMC article.
-
Anomaly detection in encrypted network traffic using self-supervised learning.Sci Rep. 2025 Jul 22;15(1):26585. doi: 10.1038/s41598-025-08568-0. Sci Rep. 2025. PMID: 40695909 Free PMC article.
-
Influence of Human Factors on Cyber Security within Healthcare Organisations: A Systematic Review.Sensors (Basel). 2021 Jul 28;21(15):5119. doi: 10.3390/s21155119. Sensors (Basel). 2021. PMID: 34372354 Free PMC article.
-
A Scoping Review of the Observed and Perceived Functional Impacts Associated With Language and Learning Disorders in School-Aged Children.Int J Lang Commun Disord. 2025 Jul-Aug;60(4):e70086. doi: 10.1111/1460-6984.70086. Int J Lang Commun Disord. 2025. PMID: 40653909 Free PMC article.
References
-
- Achiam J., Adler S., Agarwal S., Ahmad L., Akkaya I., Aleman F. L., et al. (2023). Gpt-4 technical report. arXiv preprint arXiv:2303.08774.
-
- Ajagbe S. A., Awotunde J. B., Florez H. (2024). Intrusion detection: a comparison study of machine learning models using unbalanced dataset. SN Comput. Sci. 5:1028. 10.1007/s42979-024-03369-0 - DOI
-
- Alrahis L., Knechtel J., Sinanoglu O. (2023). “Graph neural networks: a powerful and versatile tool for advancing design, reliability, and security of ICS,” in Proceedings of the 28th Asia and South Pacific Design Automation Conference, 83–90. 10.1145/3566097.3568345 - DOI
-
- Bastian N., Bierbrauer D., McKenzie M., Nack E. (2023). ACI IoT Network Traffic Dataset 2023. 10.21227/qacj-3x32 - DOI
-
- Bhavsar M., Roy K., Kelly J., Olusola O. (2023). Anomaly-based intrusion detection system for iot application. Discover Internet Things 3:5. 10.1007/s43926-023-00034-5 - DOI
LinkOut - more resources
Full Text Sources