(H-DIR)2: A Scalable Entropy-Based Framework for Anomaly Detection and Cybersecurity in Cloud IoT Data Centers
- PMID: 40808005
- PMCID: PMC12349297
- DOI: 10.3390/s25154841
(H-DIR)2: A Scalable Entropy-Based Framework for Anomaly Detection and Cybersecurity in Cloud IoT Data Centers
Abstract
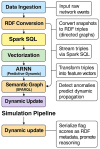
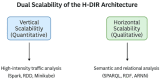
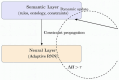
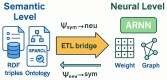
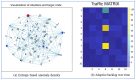
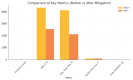
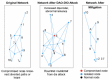
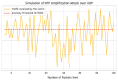
Modern cloud-based Internet of Things (IoT) infrastructures face increasingly sophisticated and diverse cyber threats that challenge traditional detection systems in terms of scalability, adaptability, and explainability. In this paper, we present (H-DIR)2, a hybrid entropy-based framework designed to detect and mitigate anomalies in large-scale heterogeneous networks. The framework combines Shannon entropy analysis with Associated Random Neural Networks (ARNNs) and integrates semantic reasoning through RDF/SPARQL, all embedded within a distributed Apache Spark 3.5.0 pipeline. We validate (H-DIR)2 across three critical attack scenarios-SYN Flood (TCP), DAO-DIO (RPL), and NTP amplification (UDP)-using real-world datasets. The system achieves a mean detection latency of 247 ms and an AUC of 0.978 for SYN floods. For DAO-DIO manipulations, it increases the packet delivery ratio from 81.2% to 96.4% (p < 0.01), and for NTP amplification, it reduces the peak load by 88%. The framework achieves vertical scalability across millions of endpoints and horizontal scalability on datasets exceeding 10 TB. All code, datasets, and Docker images are provided to ensure full reproducibility. By coupling adaptive neural inference with semantic explainability, (H-DIR)2 offers a transparent and scalable solution for cloud-IoT cybersecurity, establishing a robust baseline for future developments in edge-aware and zero-day threat detection.
Keywords: RDF/SPARQL explainability; associated random neural network (ARNN); cloud–IoT security; entropy-based anomaly detection; hybrid distributed information retrieval; semantic adaptive cyber defense; sub-second detection latency.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
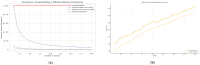
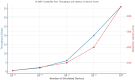
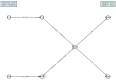
References
-
- Mirsky Y., Doitshman T., Elovici Y., Shabtai A. Kitsune: An ensemble of autoencoders for online network intrusion detection. arXiv. 2018 doi: 10.48550/arXiv.1802.09089.1802.09089 - DOI
-
- Sicari S., Rizzardi A., Coen-Porisini A. 5G in the Internet of Things Era: An Overview on Security and Privacy Challenges. Comput. Netw. 2020;179:107345. doi: 10.1016/j.comnet.2020.107345. - DOI
-
- García-Teodoro P., Díaz-Verdejo J., Maciá-Fernández G., Vázquez E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Comput. Secur. 2009;28:18–28. doi: 10.1016/j.cose.2008.08.003. - DOI
-
- Feily M., Shahrestani A., Ramadass S. A survey of botnet and botnet detection; Proceedings of the 2009 Third International Conference on Emerging Security Information, Systems, and Technologies; Athens, Greece. 18–23 June 2009; pp. 268–273.
-
- Kurtz N., Song J. Cross-entropy-based adaptive importance sampling using Gaussian mixture. Struct. Saf. 2013;42:35–44. doi: 10.1016/j.strusafe.2013.01.006. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources
Miscellaneous

