A Multi-Class Intrusion Detection System for DDoS Attacks in IoT Networks Using Deep Learning and Transformers
- PMID: 40808008
- PMCID: PMC12349258
- DOI: 10.3390/s25154845
A Multi-Class Intrusion Detection System for DDoS Attacks in IoT Networks Using Deep Learning and Transformers
Abstract
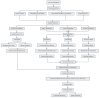
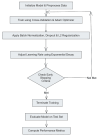
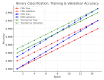
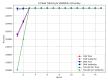
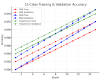
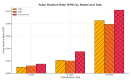
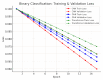
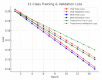
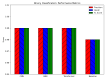
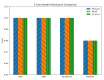
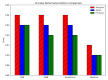
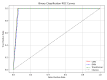
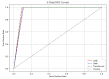
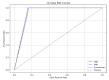
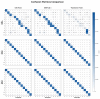
The rapid proliferation of Internet of Things (IoT) devices has significantly increased vulnerability to Distributed Denial of Service (DDoS) attacks, which can severely disrupt network operations. DDoS attacks in IoT networks disrupt communication and compromise service availability, causing severe operational and economic losses. In this paper, we present a Deep Learning (DL)-based Intrusion Detection System (IDS) tailored for IoT environments. Our system employs three architectures-Convolutional Neural Networks (CNNs), Deep Neural Networks (DNNs), and Transformer-based models-to perform binary, three-class, and 12-class classification tasks on the CiC IoT 2023 dataset. Data preprocessing includes log normalization to stabilize feature distributions and SMOTE-based oversampling to mitigate class imbalance. Experiments on the CIC-IoT 2023 dataset show that, in the binary classification task, the DNN achieved 99.2% accuracy, the CNN 99.0%, and the Transformer 98.8%. In three-class classification (benign, DDoS, and non-DDoS), all models attained near-perfect performance (approximately 99.9-100%). In the 12-class scenario (benign plus 12 attack types), the DNN, CNN, and Transformer reached 93.0%, 92.7%, and 92.5% accuracy, respectively. The high precision, recall, and ROC-AUC values corroborate the efficacy and generalizability of our approach for IoT DDoS detection. Comparative analysis indicates that our proposed IDS outperforms state-of-the-art methods in terms of detection accuracy and efficiency. These results underscore the potential of integrating advanced DL models into IDS frameworks, thereby providing a scalable and effective solution to secure IoT networks against evolving DDoS threats. Future work will explore further enhancements, including the use of deeper Transformer architectures and cross-dataset validation, to ensure robustness in real-world deployments.
Keywords: Convolutional Neural Network; Deep Learning; Distributed Denial of Service; Internet of Things security; Intrusion Detection System; Synthetic Minority Over-sampling Technique; Transformer; anomaly detection.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures


Similar articles
-
Enhancing anomaly detection and prevention in Internet of Things (IoT) using deep neural networks and blockchain based cyber security.Sci Rep. 2025 Jul 1;15(1):22369. doi: 10.1038/s41598-025-04164-4. Sci Rep. 2025. PMID: 40593899 Free PMC article.
-
DDoS classification of network traffic in software defined networking SDN using a hybrid convolutional and gated recurrent neural network.Sci Rep. 2025 Aug 9;15(1):29122. doi: 10.1038/s41598-025-13754-1. Sci Rep. 2025. PMID: 40781265 Free PMC article.
-
Blockchain enhanced distributed denial of service detection in IoT using deep learning and evolutionary computation.Sci Rep. 2025 Jul 2;15(1):22537. doi: 10.1038/s41598-025-06568-8. Sci Rep. 2025. PMID: 40593035 Free PMC article.
-
EEG-based classification of individuals with neuropsychiatric disorders using deep neural networks: A systematic review of current status and future directions.Comput Methods Programs Biomed. 2023 Oct;240:107683. doi: 10.1016/j.cmpb.2023.107683. Epub 2023 Jun 20. Comput Methods Programs Biomed. 2023. PMID: 37406421
-
Transformers for Neuroimage Segmentation: Scoping Review.J Med Internet Res. 2025 Jan 29;27:e57723. doi: 10.2196/57723. J Med Internet Res. 2025. PMID: 39879621 Free PMC article.
References
-
- Choudhary V., Guha P., Pau G., Mishra S. An overview of smart agriculture using internet of things (IoT) and web services. Environ. Sustain. Indic. 2025;26:100607. doi: 10.1016/j.indic.2025.100607. - DOI
-
- Alfatemi A., Rahouti M., Hsu D.F., Schweikert C., Ghani N., Solyman A., Assaqty M.I.S. Identifying Distributed Denial of Service Attacks through Multi-Model Deep Learning Fusion and Combinatorial Analysis. J. Netw. Syst. Manag. 2025;33:8. doi: 10.1007/s10922-024-09882-0. - DOI
-
- Xiao J., Sun R., Liu J. MLDDoS: A distributed denial of service attack detection method using multi-level sketch. J. Supercomput. 2025;81:1–36. doi: 10.1007/s11227-025-06942-3. - DOI
-
- Maiwada U.D., Danyaro K.U., Liew M., Alashhab A.A., Sarlan A.B. Convergence of Artificial Intelligence and Internet of Things for Industrial Automation. CRC Press; Boca Raton, FL, USA: 2025. Security concerns with IoT: Detecting DDoS attacks in IoT environments; pp. 152–162.
LinkOut - more resources
Full Text Sources
Miscellaneous

