A Novel One-Dimensional Chaotic System for Image Encryption Through the Three-Strand Structure of DNA
- PMID: 40870248
- PMCID: PMC12385667
- DOI: 10.3390/e27080776
A Novel One-Dimensional Chaotic System for Image Encryption Through the Three-Strand Structure of DNA
Abstract
Digital images have been widely applied in fields such as mobile devices, the Internet of Things, and medical imaging. Although significant progress has been made in image encryption technology, it still faces many challenges, such as attackers using powerful computing resources and advanced algorithms to crack encryption systems. To address these challenges, this paper proposes a novel image encryption algorithm based on one-dimensional sawtooth wave chaotic system (1D-SAW) and the three-strand structure of DNA. Firstly, a new 1D-SAW chaotic system was designed. By introducing nonlinear terms and periodic disturbances, this system is capable of generating chaotic sequences with high randomness and initial value sensitivity. Secondly, a new diffusion rule based on the three-strand structure of DNA is proposed. Compared with the traditional DNA encoding and XOR operation, this rule further enhances the complexity and anti-attack ability of the encryption process. Finally, the security and randomness of the 1D-SAW and image encryption algorithms were verified through various tests. Results show that this method exhibits better performance in resisting statistical attacks and differential attacks.
Keywords: SHA-256 hash function; one-dimensional chaotic system; security analysis; three-stranded structure of DNA.
Conflict of interest statement
The authors declare no conflicts of interest regarding the publication of this paper.
Figures
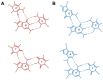


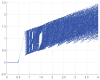
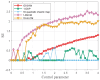

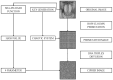




Similar articles
-
Enhancing AES image encryption with a three-dimensional hyperchaotic system for increased security and efficiency.PLoS One. 2025 Jul 18;20(7):e0328297. doi: 10.1371/journal.pone.0328297. eCollection 2025. PLoS One. 2025. PMID: 40680055 Free PMC article.
-
Enhanced security for medical images using a new 5D hyper chaotic map and deep learning based segmentation.Sci Rep. 2025 Jul 2;15(1):22628. doi: 10.1038/s41598-025-04906-4. Sci Rep. 2025. PMID: 40593969 Free PMC article.
-
Prescription of Controlled Substances: Benefits and Risks.2025 Jul 6. In: StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2025 Jan–. 2025 Jul 6. In: StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing; 2025 Jan–. PMID: 30726003 Free Books & Documents.
-
The Black Book of Psychotropic Dosing and Monitoring.Psychopharmacol Bull. 2024 Jul 8;54(3):8-59. Psychopharmacol Bull. 2024. PMID: 38993656 Free PMC article. Review.
-
Single-incision sling operations for urinary incontinence in women.Cochrane Database Syst Rev. 2017 Jul 26;7(7):CD008709. doi: 10.1002/14651858.CD008709.pub3. Cochrane Database Syst Rev. 2017. Update in: Cochrane Database Syst Rev. 2023 Oct 27;10:CD008709. doi: 10.1002/14651858.CD008709.pub4. PMID: 28746980 Free PMC article. Updated.
References
-
- Shannon C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949;28:656–715. doi: 10.1002/j.1538-7305.1949.tb00928.x. - DOI
-
- Fridrich J. Symmetric Ciphers Based on Two-Dimensional Chaotic Maps. Int. J. Bifurc. Chaos. 1998;8:1259–1284. doi: 10.1142/S021812749800098X. - DOI
-
- Liu W., Sun K., Wang H., Li B., Chen Y. Inverse Proportional Chaotification Model for Image Encryption in IoT Scenarios. IEEE Trans. Circuits Syst. I Regul. Pap. 2024;72:254–264. doi: 10.1109/TCSI.2024.3511675. - DOI
-
- Wan H., Zhou L., Chen H., Pang D.M., You Z.Q., Wang C., Wang Y., Huang G. Furniture image protection scheme based on chaotic generating matrix encryption and filter combined with genetic algorithm noise reduction. Phys. Scr. 2025;100:065221. doi: 10.1088/1402-4896/add5a4. - DOI
-
- Erkan U., Toktas A., Memis S., Toktas F., Lai Q., Wen H., Gao S. OSMRD-IE: Octal-Based Shuffling and Multilayer Rotational Diffusing Image Encryption Using 2-D Hybrid Michalewicz–Ackley Map. IEEE Internet Things J. 2024;11:35113–35123. doi: 10.1109/JIOT.2024.3432494. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources

