A lightweight multi round confusion-diffusion cryptosystem for securing images using a modified 5D chaotic system
- PMID: 40885745
- PMCID: PMC12398579
- DOI: 10.1038/s41598-025-13290-y
A lightweight multi round confusion-diffusion cryptosystem for securing images using a modified 5D chaotic system
Abstract
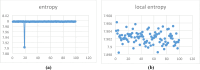
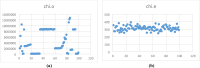
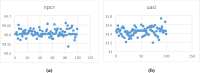
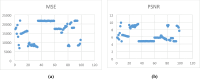
In recent years, technological advancements have made the transmission of confidential information spooky. This research proposes a modified 5D chaotic map and a new image encryption algorithm based on an integrated chaotic system developed with SHA-512 hashing and a confusion-diffusion architecture. The modified 5D chaotic map provides randomness, and its performance is evaluated through a bifurcation diagram and Lyapunov exponent. The randomness of chaotic sequences is validated through the NIST test. The multi-round diffusion and permutation incorporating the proposed chaotic sequences significantly enhances security by destroying pixel correlation among pixels. The encryption algorithm is validated through performance metric analysis, yielding NPCR of 99.6069%, UACI of 33.4284%, and entropy of 7.99442. These values depict advanced security features needed for various multimedia, medical, and military applications. Therefore, this approach reveals the extent to which chaotic encryption systems provide digital image protection in high-risk communication environments.
Keywords: Chaotic maps; Confusion-diffusion; Digital security; Image encryption; Multimedia protection; SHA-512.
© 2025. The Author(s).
Conflict of interest statement
Declarations. Competing interests: The authors declare no competing interests. Ethics approval: This article contains no studies with human participants performed by authors. Data availability: The datasets generated during and/or analysed during the current study are available from the corresponding author upon reasonable request. The sources of the sample images are downloaded from https://sipi.usc.edu/database/database.php?volume=aerials , https://www.kaggle.com/datasets/samahsadiq/benign-and-malicious-qr-codes , https://www.dicomlibrary.com/ , http://bias.csr.unibo.it/fvc2000/download.asp .
Figures

















Similar articles
-
Enhanced security for medical images using a new 5D hyper chaotic map and deep learning based segmentation.Sci Rep. 2025 Jul 2;15(1):22628. doi: 10.1038/s41598-025-04906-4. Sci Rep. 2025. PMID: 40593969 Free PMC article.
-
A novel 2D MTMHM based key generation for enhanced security in medical image communication.Sci Rep. 2025 Jul 14;15(1):25411. doi: 10.1038/s41598-025-10485-1. Sci Rep. 2025. PMID: 40659745 Free PMC article.
-
Robust Image Encryption with 2D Hyperchaotic Map and Dynamic DNA-Zigzag Encoding.Entropy (Basel). 2025 Jun 6;27(6):606. doi: 10.3390/e27060606. Entropy (Basel). 2025. PMID: 40566193 Free PMC article.
-
Medical Image Encryption Using Chaotic Mechanisms: A Study.Bioengineering (Basel). 2025 Jul 4;12(7):734. doi: 10.3390/bioengineering12070734. Bioengineering (Basel). 2025. PMID: 40722426 Free PMC article. Review.
-
NIH Consensus Statement on Management of Hepatitis C: 2002.NIH Consens State Sci Statements. 2002 Jun 10-12;19(3):1-46. NIH Consens State Sci Statements. 2002. PMID: 14768714
References
-
- Corporation, I. Cost of a data breach report 2024. IBM Secur. 1–73 (2021).
-
- Mansouri, A. et al. A secure medical image encryption algorithm for IoMT using a Quadratic-Sine chaotic map and pseudo-parallel confusion-diffusion mechanism. Expert Syst. Appl.270, 126521 (2025).
-
- Jain, S., Samal, A., Sharma, A., Khurana, M. & Sharma, B. Advanced image security through chaotic system-based encryption and fisher-yates matrix shuffling. Optik327, 172304 (2025).
-
- Benyahia, K., Khobzaoui, A. & Benbakreti, S. Hybrid image encryption: leveraging DNA sequencing and Lorenz chaotic dynamics for enhanced security. Clust. Comput.28, 218 (2025).
LinkOut - more resources
Full Text Sources

