Multilayered SDN security with MAC authentication and GAN-based intrusion detection
- PMID: 40906752
- PMCID: PMC12410795
- DOI: 10.1371/journal.pone.0331470
Multilayered SDN security with MAC authentication and GAN-based intrusion detection
Abstract
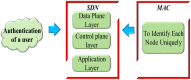
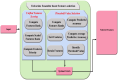
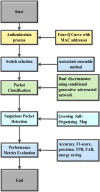
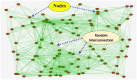
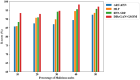
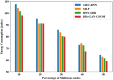
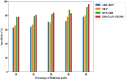
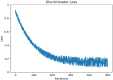
Computer networks are highly vulnerable to cybersecurity intrusions. Likewise, software-defined networks (SDN), which enable 5G users to broadcast sensitive data, have become a primary target for vulnerability. To protect the network security against attacks, various security protocols, including authorization, the authentication process, and intrusion detection techniques, are essential. However, there are several intrusion detection strategies, but the most prevalent methods show low accuracy and high false positives. To overcome these problems, this research work presents a novel four-Q curve authentication system based on Media Access Control (MAC) addresses for a multilayered SDN intrusion detection system utilizing deep learning techniques to identify and prevent attacks. The Four-Q curve authentication system leverages elliptic curve cryptography, a high-performance algorithm that improves authentication security and computational efficiency. Initially, Four-Q curve authentication is performed, followed by univariate ensemble feature selection to select optimal switches. Then, the data collected through the switches are classified as normal, assault, and suspect packets based on the Dual Discriminator Conditional Generative Adversarial Network (DDcGAN) approach. Further, the optimization of DDcGAN is accomplished using the Sheep Flock Optimization Algorithm (SFOA), whereas suspicious packets are categorized using the Growing Self-Organizing Map (GSOM). The DDcGAN-based intrusion detection system outperforms the state-of-the-art approaches in terms of accuracy, precision, F1 score, sensitivity, false-positive rate, power consumption, and network throughput. It achieved an accuracy of 98.29%, an F1 score of 0.975, and a precision of 95.8%. The system's true positive rate attained 99.04% at 50% malicious nodes, while the false alarm rate was as low as 2.05% under the same conditions. Moreover, the system exhibits 4.5% energy savings when compared to existing approaches.
Copyright: © 2025 Kiran Singh Nayak, Bhattacharyya. This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures








References
-
- Nayak NKS, Bhattacharyya B. An Intrusion Detection System for 5G SDN Network Utilizing Binarized Deep Spiking Capsule Fire Hawk Neural Networks and Blockchain Technology. Future Internet. 2024;16(10):359. doi: 10.3390/fi16100359 - DOI
-
- Ravi V, Chaganti R, Alazab M. Recurrent deep learning-based feature fusion ensemble meta-classifier approach for intelligent network intrusion detection system. Computers and Electrical Engineering. 2022;102:108156. doi: 10.1016/j.compeleceng.2022.108156 - DOI
-
- Yungaicela-Naula NM, Vargas-Rosales C, Pérez-Díaz JA, Carrera DF. A flexible SDN-based framework for slow-rate DDoS attack mitigation by using deep reinforcement learning. Journal of Network and Computer Applications. 2022;205:103444. doi: 10.1016/j.jnca.2022.103444 - DOI
-
- Naqash T, Shah SH, Islam MNU. Statistical Analysis Based Intrusion Detection System for Ultra-High-Speed Software Defined Network. Int J Parallel Prog. 2021;50(1):89–114. doi: 10.1007/s10766-021-00715-0 - DOI
-
- Birkinshaw C, Rouka E, Vassilakis VG. Implementing an intrusion detection and prevention system using software-defined networking: Defending against port-scanning and denial-of-service attacks. Journal of Network and Computer Applications. 2019;136:71–85. doi: 10.1016/j.jnca.2019.03.005 - DOI
MeSH terms
LinkOut - more resources
Full Text Sources

